With the rise in the usage of mobile phones, mobile applications have become an integral part of our lives. However, the accelerating demand for mobile apps has also raised concerns about application security. There are a lot of cyberattacks that take place daily, increasing the concern among businesses.
An unsecured app can be vulnerable to any online malicious attack. These attacks can be harmful to customers’ crucial data. These can leave users at risk of losing personal information.
According to research, due to COVID-19, cybercrime has increased by up to 600%. And the global annual cost of cybercrime is estimated to be $6 trillion a year. By 2015, the cost of cybercrime was approximately $10.5 trillion annually.
The top 5 online crimes reported in 2021 were:
- Extortion
- Identity theft
- Personal data breach
- Non-payment
- Phishing attacks
These stats were an eye-opener and informed everyone about the importance of mobile application security.
However, malicious cybercriminals can access over 300 app stores to create and spread fake, malware-infused, and fraudulent applications. In addition, experts say that 77% of financial apps have vulnerabilities that can lead to a data breach.
Reasons to secure your mobile apps
Here are a few top-notch reasons to help you understand why securing your mobile apps is essential for development.
- Data Breaching: Recent research says that 90% of all mobile applications are prone to attack by malicious threats. So to keep the apps safe, it is crucial to take security measures. Unsecured apps are more vulnerable to malicious attacks if you compromise security measures. Mobile apps store valuable information such as credentials, passwords, and payment information of users. If data gets compromised in a data breach, it can cause devastating results for both users and the business.
- Malicious apps: Malicious software helps hackers or cybercriminals gain access to the user’s personal information. Malicious malware-infused apps can attack your device and take users’ data, financial accounts, identity theft, and more. Such malware-infused apps can steal important information. Not only that, these apps are powerful enough to delete your crucial, personal, and sensitive information.
- Unauthorized access: Mobile apps are more prone to vulnerability exploitation attacks that can lead to unauthorized access and other complications. Unauthorized access occurs when a cybercriminal gains access to your mobile apps using various methods or techniques, such as exploiting weak passwords, vulnerable code, and more. Insecure apps are more prone to be used by malicious third parties. Such insecure apps are easy to hack and can give access to confidential or sensitive data. And, this can affect your business in many ways.
- Inherent vulnerabilities: Mobile apps developed without following necessary security measures are more at risk of being attacked due to in-built security flaws and loopholes. This can put your whole business at risk. Due to the vulnerabilities in mobile apps, it is crucial to keep the mobile apps under constant monitoring using in-app protection solution. Some businesses tend to neglect security measures and do not follow best practices while developing the apps. They are more at risk of getting attacked.
Security measures to take while developing a mobile application
Mobile app security is more critical than we think. Nowadays, employees often merge their professional and personal interests into a single device. Here are a few security measures or practices you must take while developing a mobile app.
- Data Encryption: Data encryption converts data or information into an encrypted form that can only be understood or read by the authorized person. The authorized personnel has a data encryption key with them. It helps them read the message. It is an effective method to protect the data from any breach or misuse. Even if the hacker accesses the data, they can not understand it, and the data will not be of their use.
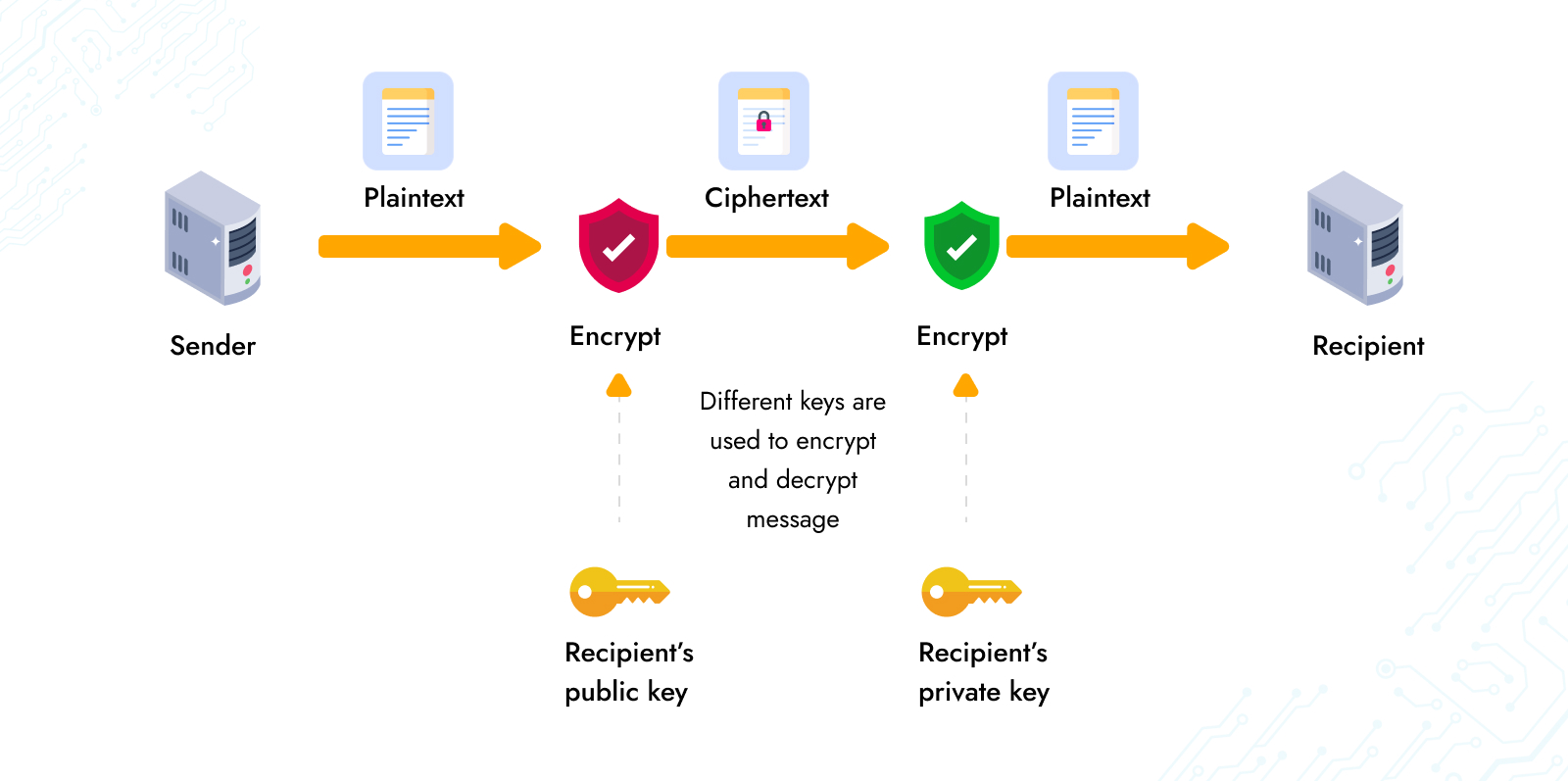
It is crucial to encrypt the data but ensure to keep the level of encryption minimal to avoid any issue with the end-user device.
- Increased Code Security: The application code is the most crucial part of security as it controls all the features and functionalities of your app. If a hacker takes access to the code, it can be disastrous to the organization. They can misuse the code by making changes in the app, which can change the whole functionality of the app. So it is crucial to follow a few practices like removing the unnecessary metadata data and debugging information from the code. These practices can help you make your code less vulnerable to a security breach and help in enhancing the performance of the code.
Moreover, developers can use encryption to make the code more secure. Also, you can add unconventional labels for your classes and modules to divert hackers.
- Use of known third-party libraries: With the growing use of third-party libraries in mobile app development, developers use many third-party libraries to make their lives easy. But it is crucial to validate the credentials of any third-party library before integrating them into the project.
Moreover, businesses can not ignore the fact that open-source is freely available to anyone, and libraries are unsafe. There is a high risk that these libraries can inject the virus into your app. Such libraries when used in mobile apps can make the code vulnerable and can be attacked by hackers.
So, it is suggested to only use well-known libraries, and their latest versions. The latest versions contain recent improvements and security updates that can avoid potential security breaches that can harm your code.
- Use Authorized APIs: An API is an interface that provides a common platform that enables computer programs to communicate with each other. It defines a few methods that help you make calls or requests to access other resources and allows you to execute the functions.
The mobile apps also have API-mechanism that helps the apps process. These apps are highly prone to attacks by hackers. So it is crucial to only approve the secure APIs in your apps.
To protect the apps from malicious attacks, developers can assign API keys to every application, making the overall app secure. Moreover, developers can monitor the usage of API keys and integrate an Application Programming Interface Gateway to tighten security. Also, developers can use better authentication methods, such as a token or 2-factor authentication to ensure that only authorized persons can alter or make changes in the code.
- High-level Authentication: These systems are the most critical part of mobile application security. They are used to provide access to users for a specific resource and keep the app secure. Businesses must pay attention to adding necessary checks, control, and strong authentication methods to keep the app and the user data safe.
To keep the authentication level high, developers can use Multifaceted authentication methods that include strong static passwords, 2-Factor Authentication, Retina Scan, Biometrics, Dynamic OTP, and more.
- Tamper detection method: Nowadays, it is easy for hackers to access confidential data or reverse engineer your data code as everything is present online. So, businesses must follow strategies to implement a strong and effective tamper detection method.
The tamper detection method can track or detect any changes which happen in your code and can send an alert to the app developers or the app owners. Moreover, developers can use a checksum, logging, digital signatures, and auditing methods to detect any changes that happen in the code. These methods send alerts to developers about potential security threats.
- Controlled privileges: A token of access for specific application components is given to the authorized and designated resource. Businesses must implement a policy of “Least privilege”. This policy ensures that access is given only to the authorized person. The same principle is applied to mobile apps, and the apps should not ask for unnecessary or unauthorized privileges.
- Session management: Session management is another important aspect of mobile application security. Every mobile app creates different sessions for the users. These sessions are maintained on most apps via cookies, making them more vulnerable to any security threats.
A session is a series of HTTP requests and mobile and web apps these series of the session to communicate. It involves sharing of confidential data with authenticated users. Hence these communications must be secured by using cryptographic network communication methods. To protect from hackers, developers must ensure that the size of the cookie is adequate and should have high-security session configuration settings.
- Strong access policies: Mobile apps must remain in sync with the organization’s corporate and security policies. Developed apps must comply with the Application Stores (Apple App Store or Google Play Store). These are stores where apps must be listed once they are ready. So it is crucial to use a framework that is highly secure and must reduce the risk of malware attacks.
- Test repeatedly: Testing is certainly the most crucial step of any mobile app development process. There is no limit to testing a mobile application, the more you test the more issues you can find. Also, developers must create various test cases, based on security threats and challenges in the market to enhance the security of apps.
The apps must be tested for various use cases, hence ensuring that your app is working fine. The testing process includes:- Application Security
- Session management
- Encryption challenges
- Authorization
- Authentication
Ways to secure your mobile apps
While developing an app, ensure to take the necessary steps that help you keep the app secure. Here are a few tips that can help you secure the development of the apps.
- Data Security: Mobile app security determines the safety of customers’ data. If the security measures are not strict, hackers can easily access the crucial information of the app. So, businesses must opt for security measures such as encryption.
- User Authentication: User authentication protects your app against any unauthorized user attempt to your application. Businesses can prevent their user’s data and sensitive information from hackers or cybercriminals by using 2-Factor Authentication.
- Secure APIs: Mobile apps rely on Application Programming Interfaces (APIs) to communicate between the app and its backend services. These APIs must be secured enough to ensure that only authenticated users are allowed access. Businesses use security measures to protect their data and sensitive information against potential threats.
- Reduce Malware Threats: Malware is one of the most serious threats to your mobile app. Businesses can reduce the risk of malware entering their applications by using proper security measures such as in-built sandboxes, antivirus software, and intrusion detection systems.
Conclusion
Even though security is a never-ending concern, hackers or cybercriminals are constantly finding new ways of malicious attacks.
So, mobile app developers must stay updated with the technology and create a counter-strategy to keep the apps safe from any malicious activity. In addition, if businesses apply the above-mentioned strategies it can become difficult for hackers to penetrate your app.
Moreover, staying updated with the latest technology is crucial, but they should focus more on Cybersecurity. And it is a must to keep knowledge about innovative data and security breach practices.
The best part is that these security measures can be implemented without huge costs on the mobile application development process. We can achieve the best results for our Mobile application if we follow a holistic approach towards integrating Cybersecurity with the mobile apps.
At OZVID Technologies, we follow industry-standard mobile app security measures that ensure the reliability and integrity of the applications. We aim to provide mobile apps driven by innovation, creativity, and security with a good user experience.
Are you looking to develop apps that protect your data from all malicious attacks? Invest in us. Our proficient mobile development specialists will offer you highly secure and reliable mobile apps.



















































Share this post on: