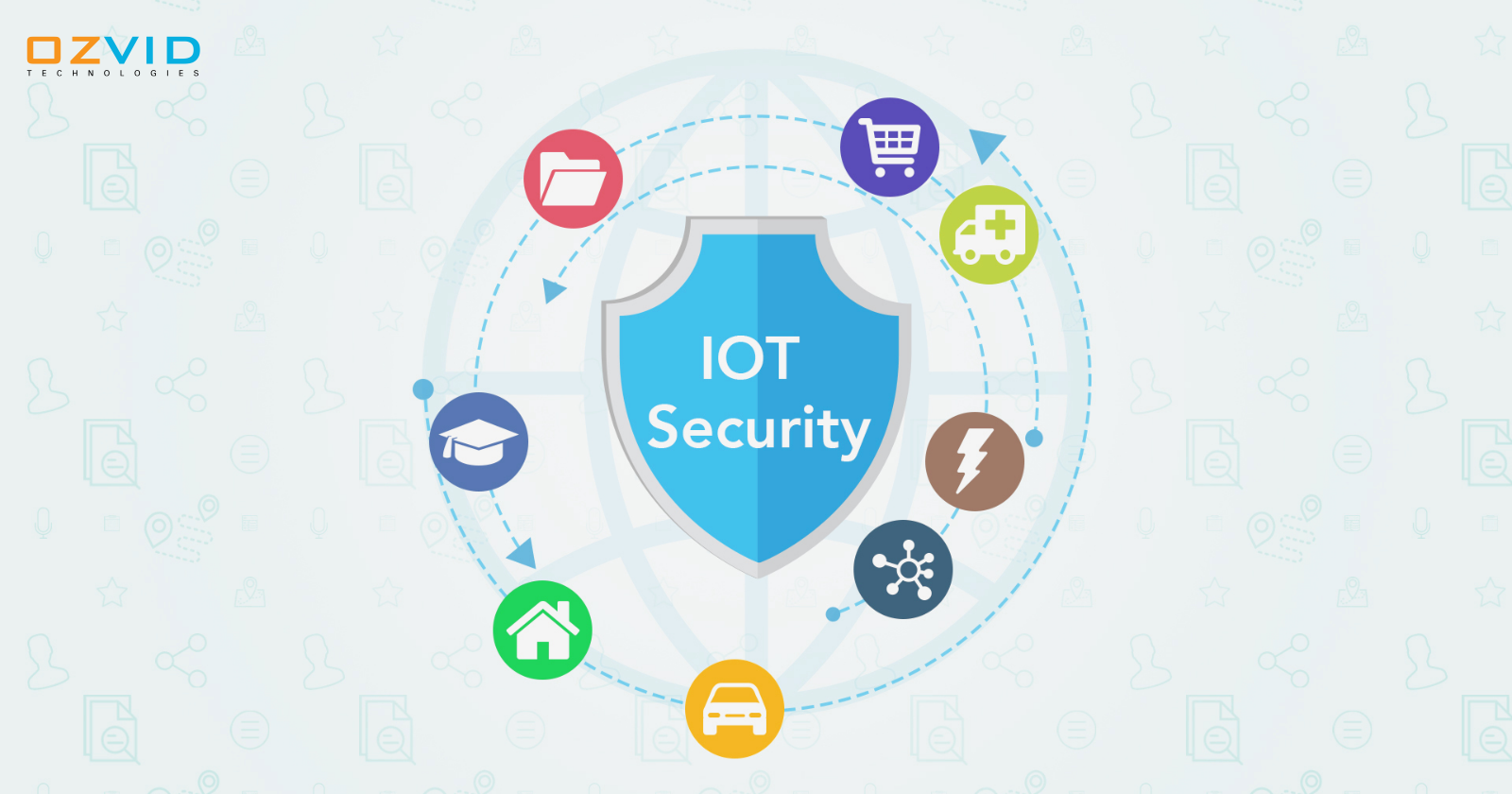
Internet of Things (IoT) boom that has made life very much simple as it has included a ton of lifeless things with the internet. Its prevalence in the present mobile-driven world is perceived by the report of Frost and Sullivan that says every person is likely to have an average of 5.1 connected devices by 2020. It just implies that the idea has tremendous conceivable outcomes and a customized IoT mobile application is important to grab them.
However, IoT is additionally the one that has made us helpless against numerous spots. The expansion of online mobile devices won't be a very good news as this will as said put tremendous strain on the systems that are not dynamic. Taking into consideration the vulnerabilities, there are numerous till now that have been reported to the IoT solution provider companies. It has additionally conveyed us the security concerns previously unthought of.
In this way, there are various IoT security factors that one should remember before developing a mobile application.
- Insecure Software: Number of individuals are not ready to set passwords that are adequate in complexity and length and their devices dependent on quite simple passwords. It will be an incredible source for hackers to hack their devices as the passwords are very easy to encrypt. So they have to follow a strong password policy that will be the base for good security. Authentication issues of information may not be straight but they will be the reason behind a security risk without a doubt.
- Network Unawareness: Numerous clients and even organizations do not have the complete information as what all is there on the system and connected to the network which prompts something being left out to complete vulnerability. Many organizations are not totally aware of what is there on the system and subsequently cannot assess if they have any IoT device that is configured wrongly. It is very hard to keep up a view like a dashboard of every single device on the system.
- Hardware and Device Related Issues: The prior devices did not use to have those processors or chips which had the capacity to encrypt or send information securely, however, in the upcoming time when it is expected upon to experience a boom in the field the makers are making their devices with the chips that are good with the IoT system. Also, the multifaceted design will require more battery power which is totally a challenge for IoT applications.
- Privacy: There are various connected devices that collect personal data: Name, DOB, address, credit card information, and so forth. A portion of the gadgets transmit that information over the system with no sort of encryption technique, which might be simple for an interceptor to trace, and read. Cloud computing services which are used by various devices are also vulnerable.
- Encryption of Data: Number of devices make use of unencrypted network services. The vast majority of devices fail to encrypt the information when they are connected to the internet. They should perform transport encryption where information change between two gadgets will be scrambled. It will be exceptionally huge to defeat security concerns.
- Secure Web: With the constant cross-site scripting, simple default passwords and weak session management are the concerns when it comes to the user web interface. These are the plus points for hackers to effectively recognize accounts of users and misuse it for their benefits.
How to improve IoT security now?
- Perform clear emphasis on security from the day one is always a superior
- Implementation of secure access control as well as device authentication
- Get important updates regularly throughout the lifecycle
- Be ready for probable security breaches sooner or later
- Include built-in security features
How to Find a Reliable IoT App Development Company
This is a question that perplexes each business visionary. After having an IoT application idea, entrepreneurs begin finding a reliable and experienced IoT application development company. However, here is a catch: you have to discover an organization that can keep up the subtle balance between cost-effectiveness and quality of an IoT mobile application. At the end of the day, you should discover an organization that builds up a feature-rich and impeccable IoT mobile application for your business in a cost-efficient manner.

















































Share this post on: